Without SIP Security, Call Data Is An Open Book to Hackers
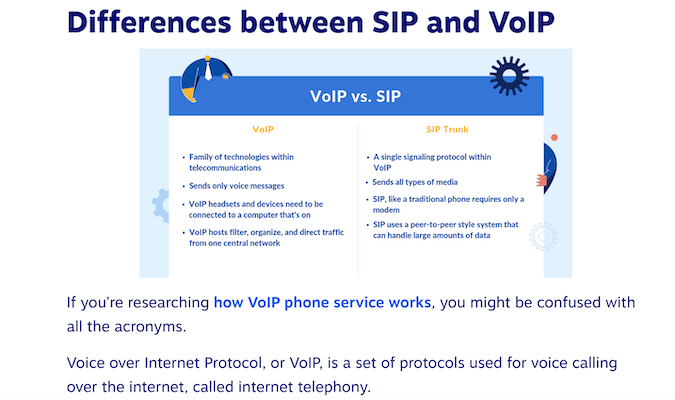
Session Initiation Protocol (SIP) is the specific sequence of steps required to begin or terminate the transmission of voice or video data between two or more devices on a cloud-based network. Over time, the majority of business owners are moving on from the older, copper wire-based telecommunications systems in favor of newer technology such as Voice over Internet Protocol (VoIP), which instead enables the same reliable communication over the internet.
SIP is an integral piece of VoIP technology, as it gives business owners and call center service providers the ability to offer an abundance of functionality at a fraction of traditional landline costs. Thus, gone are the days when you had to pay a phone company a monthly fee for tens or even hundreds of physical lines held for your business and employees to use. Now, with the help of SIP, many of the top VoIP vendors (such as RingCentral or Nextiva) can establish a virtual line whenever you need it, charging only for the actual time spent on each line.
Altogether, SIP technology presents network users with a fast and reliable means of transmitting voice and video data between smartphones, computers, and even desk phones. However, this open line can be exploited by hackers if you aren’t careful.

Why SIP Security is a Must
SIP was not originally developed with personal security in mind. In fact, it’s a text-based protocol that looks a lot like the regular HyperText Markup Language (HTML) we see on websites and in emails. As a result, all of the information contained in each SIP transmission—including specific device information, data types, and network details—can easily be intercepted and read. All it takes is one hacker with the basic skills to eavesdrop on your internet network.
If you’re wondering why a hacker might bother targeting business IP networks, the answer lies both in the data you’re transmitting and in the capabilities of your system. If your call, text, or voice data includes login credentials or other sensitive information, it could be useful for hacking personal or client accounts.
Alternatively, a hacker may also want to capture the exclusive use of your IP port, essentially taking your phone line hostage. If successful, they can then call hundreds of premium rate numbers to expensive international destinations. This scam is known as toll fraud, and it earns hackers billions per year from complicit service providers, often costing business owners more in damages than credit card fraud.
From the inception of SIP technology, opportunistic criminals have developed a variety of common attack maneuvers that are now widely known throughout the IT world. These include:
- Man-in-the-Middle Attacks: An unsecured Wi-Fi connection can be intercepted, rerouting calls to another server where your system becomes vulnerable to harmful malware and viruses
- SIP Register Flood: When your VoIP network is overwhelmed by fake connection requests to use up your internet bandwidth
- Denial of Service (DoS): Your entire network is held hostage, barring you from entry without making payment
- Call Tampering: A noise packet can be inserted into your data stream, ruining call quality
- Vishing: Similar to text or email phishing but on a VoIP network, sensitive information is solicited through a URL link or phone number
- Call Hijacking: Your Wi-Fi hotspot can be accessed to steal information or siphon internet service
- ID Spoofing: A hacker mimics a phone number from a trusted source to gain access to your data
SIP Security: SIPS and SRTP
Once SIP establishes a connection between or among device users, Real time Transfer Protocol (RTP) is used to transmit voice or video data, with SIP terminating the call at the end. Due to how HTML is used in both protocols, they are highly susceptible to interception and corruption. To combat this, IT experts developed SIP Secure (SIPS) and Secure RTP (SRTP) to protect each aspect of your calls—including both the connection details and the call data itself.
SIPS opens a virtual call line using Transport Layer Security, which is the same protocol used to encrypt online payments through HTTPS websites. In this case, it establishes a secure channel and authenticates users while encrypting their private details and preserving the integrity of the data.
Likewise, SRTP does the same thing during the data transmission in a handshake-like process between user ports. Each call generates a unique algorithm key that encrypts and decrypts data as it is transmitted and received at its destination port. The result is a secure connection from the time the call is initiated to the moment of termination.
Although both protocols are the current gold standards for protecting virtual communications networks from cyberattacks, they are only compatible with devices that support SIPS and SRTP encryption. Still, experts agree that such privacy tools should be employed when operating on a Local Area Network (LAN) or cloud-based network where attacks are likely.
SIP Security Best Practices
It is up to your specific VoIP provider whether or not SIPS and SRTP protocols are engaged in all data transmissions. You can easily find out by asking your customer service representative if the service uses end-to-end encryption and whether or not calls ever transmit data over the Public Switched Telephone Network (PSTN).
In addition to the security measures taken by your VoIP host, there are a number of steps you can take to further safeguard your business communications, such as:
All in all, VoIP-related capabilities like SIP help business owners maximize their telecommunications performance at a much more competitive price point than traditional landline networks.
At the same time, organizations that embrace these advanced technological solutions may unknowingly expose themselves to unforeseen losses at the hands of scammers, so it’s important to take proper precautions.
Fortunately, a bit of extra effort and insight can keep you one step ahead of the hackers, protecting the security of your call data so you enjoy the benefits of VoIP, stress-free.



